Cloud computing fundamentally relies on robust networking to ensure seamless communication, security, and resource allocation. Networking components play a pivotal role in maintaining connectivity and optimizing the performance of cloud-based applications and services.
Question to the reader:
from the above paragraph, we can see a disadvantage of cloud computing. whats that?
what is the role of networking components? -> maintains connectivity to cloud resources and optimizing the performance of cloud-based applications and services.
how do they optimize the performace of cloud applications?
-> by ensuring efficient communication, high availability, and effective resource utilization.
eg of networking components: VPC, Firewall, Load Balancing, Shared Access, and Hybrid Cloud
Virtual Private Cloud (VPC):
Virtual Private Cloud (VPC) is a crucial networking feature offered by cloud providers that enables you to create a logically isolated network within the cloud environment. It provides a controlled and secure environment for your resources.
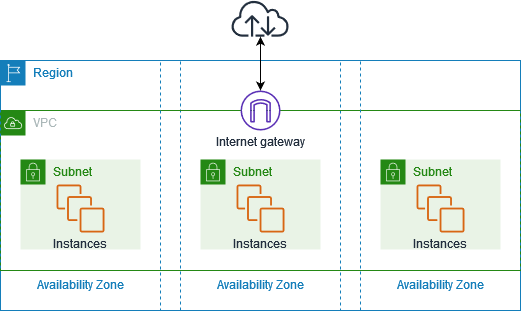
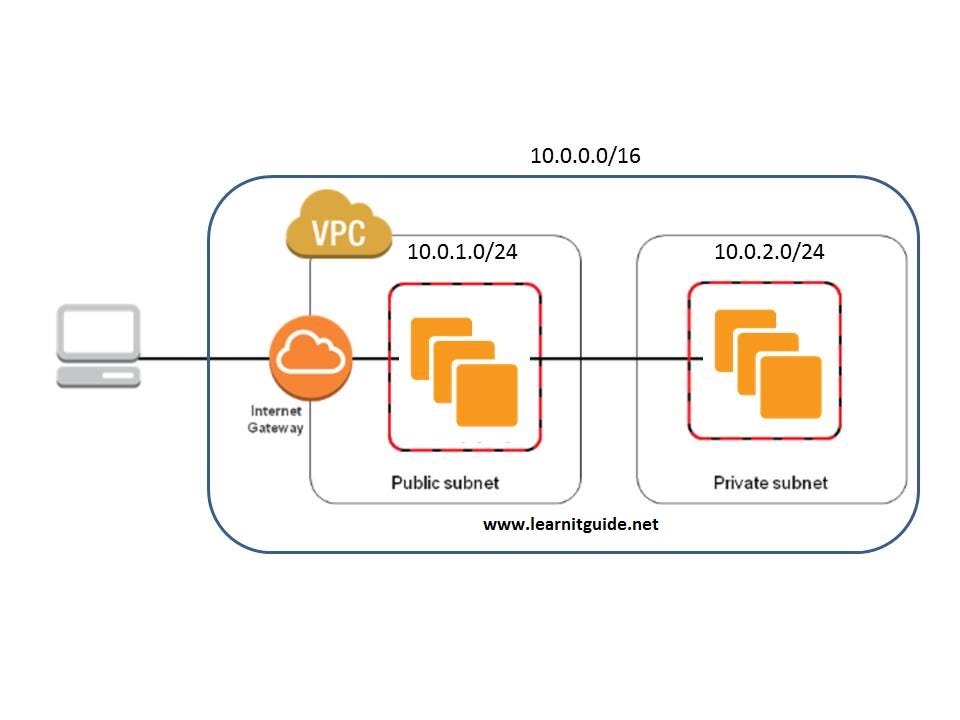
Features:
Isolation and Segmentation: VPC allows you to isolate your cloud resources, such as virtual machines, databases, and load balancers, into distinct network segments.
IP Addressing and Subnetting: You have control over IP address ranges and can create subnets within your VPC for better organization.
Security Groups and Network ACLs: VPCs offer security groups (firewall rules at the instance level) and network access control lists (ACLs) for network traffic control and security enforcement.
Private and Public Subnets: You can create private subnets for sensitive resources that don't require direct internet access, and public subnets for resources that interact with the internet.
VPN and Direct Connect: VPC supports virtual private network (VPN) connections and dedicated network connections (Direct Connect) to extend on-premises networks.
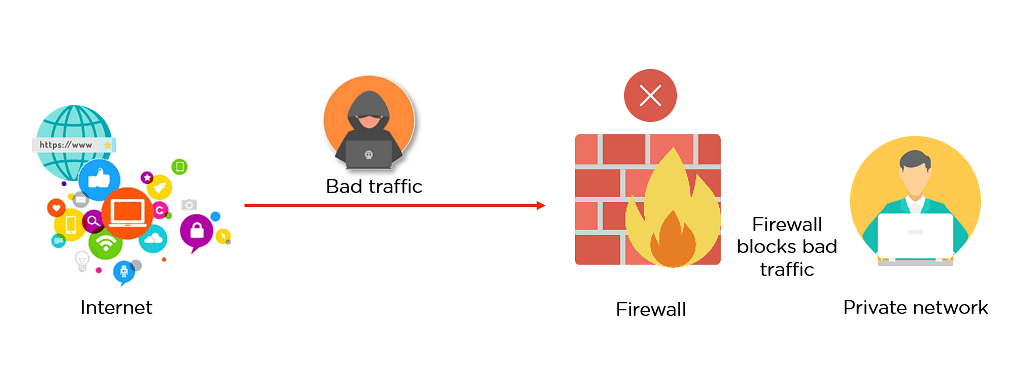
Firewall:
If a resource is connected to the Internet connection, it is vulnerable to online attacks.
Firewalls play a vital role in controlling and securing network traffic to and from cloud resources. A network firewall is based on security rules to accept or reject specific traffic. The aim of the firewall is to allow or deny the connection or request, depending on implemented rules.
Therefore, a firewall, also known as a network firewall, is capable of preventing unauthorized access to/from private networks.
Key Points:
Access Control and Filtering: Firewalls regulate incoming and outgoing network traffic based on predefined security rules.
Stateful Inspection: Modern firewalls use stateful inspection to track the state of active connections and allow or deny traffic accordingly.
- Think of a stateful inspection firewall as a smart security guard for your computer network. This guard doesn't just look at individual visitors (packets of data) coming in and out; it remembers who's visiting and what they're doing. It keeps track of ongoing conversations, like a chat between two people, and decides if the conversation is normal or suspicious.
Intrusion Detection and Prevention: Some firewalls include intrusion detection and prevention systems to identify and block suspicious activities.
- Imagine your computer network is like your home, and you have a security system that's on the lookout for strangers trying to break in. This system not only watches for anyone sneaking around your house but also listens carefully to the noises they're making. If it hears sounds like someone trying to pick the lock or break a window, it immediately raises an alarm to let you know something's wrong. Similarly, intrusion detection and prevention in firewalls are like security systems for your network. They watch for unusual activities or signs that hackers might be trying to get in. If they detect anything suspicious, they take action to stop the hackers before they cause any harm.
Application Layer Filtering: Next-generation firewalls can inspect traffic at the application layer, identifying and blocking threats more effectively.
- Think of the internet as a busy marketplace where different people are buying and selling things. Some of these people are good, but others might be trying to sell fake or harmful products. Application layer filtering is like having an expert inspector at the market who can recognize which products are safe and which are not. This inspector doesn't just look at the packaging; they examine the products closely to see if they meet the standards. Similarly, firewalls with application layer filtering can look beyond basic data packets and actually understand what different programs and websites are trying to do.
Load Balancing:
Load balancing is essential for distributing incoming network traffic across multiple resources to ensure efficient resource utilization and improved performance.
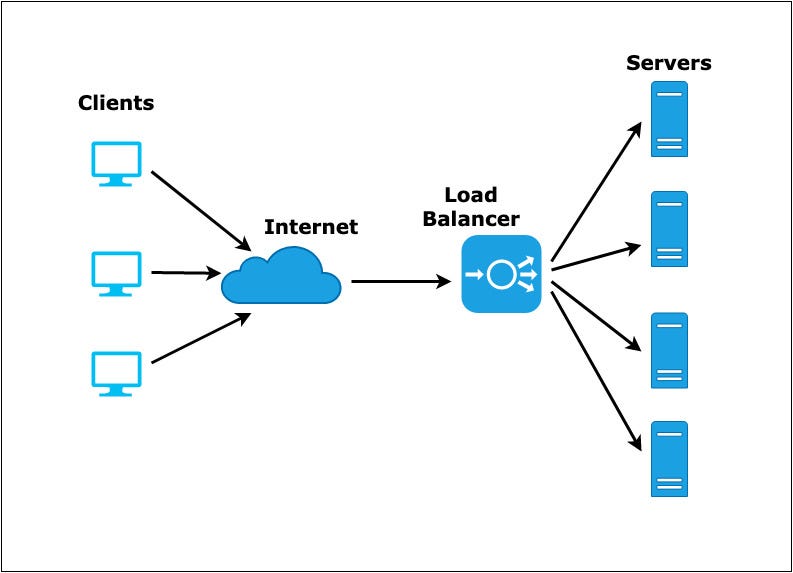
Key Points:
Types of Load Balancing: Cloud providers offer various types of load balancers: Application Load Balancers (ALB), Network Load Balancers (NLB), and Classic Load Balancers (CLB).
ALB: ALBs are designed to route traffic to different target groups based on the content of the application layer (Layer 7) of the OSI model. They are best suited for distributing traffic to multiple microservices or applications that run on the same port.
- ALBs can route traffic based on URL paths, making them suitable for hosting multiple applications on the same set of instances.
NLB: NLBs can distribute traffic at the transport layer (layer 4), making them suitable for protocols that don't require inspection of application content. used for TCP/UDP Load Balancing
CLB: CLBs were the original load balancers in AWS and operate at both the application and transport layers. They have since been mostly replaced by ALBs and NLBs
Distributing Traffic: Load balancers distribute incoming traffic across healthy instances, preventing any single instance from becoming overwhelmed.
Health Checks: Load balancers regularly check the health of instances and route traffic only to those that are responsive.
Session Persistence: Some load balancers can maintain session persistence, ensuring that requests from the same client are directed to the same backend instance.
Use Cases:
Scalability: Load balancing helps scale applications horizontally by adding instances to handle increased traffic.
High Availability: Load balancers improve availability by automatically routing traffic to healthy instances, even if some fail.
Shared Access :
Cloud networking enables shared access and collaboration on resources and data across teams and locations.

Key Points:
Collaboration Tools: Cloud providers offer collaboration tools (IAM, Access Control Lists (ACLs)) and features to allow multiple users to work together on documents, projects, and data.
Access Control: Access controls and permissions ensure that users have the appropriate level of access to resources while maintaining security.
Use Cases:
Team Collaboration: Cloud-based collaboration tools enable remote teams to work together in real time on documents and projects.
Data Sharing: Controlled access to shared data and resources ensures data integrity while promoting collaboration.
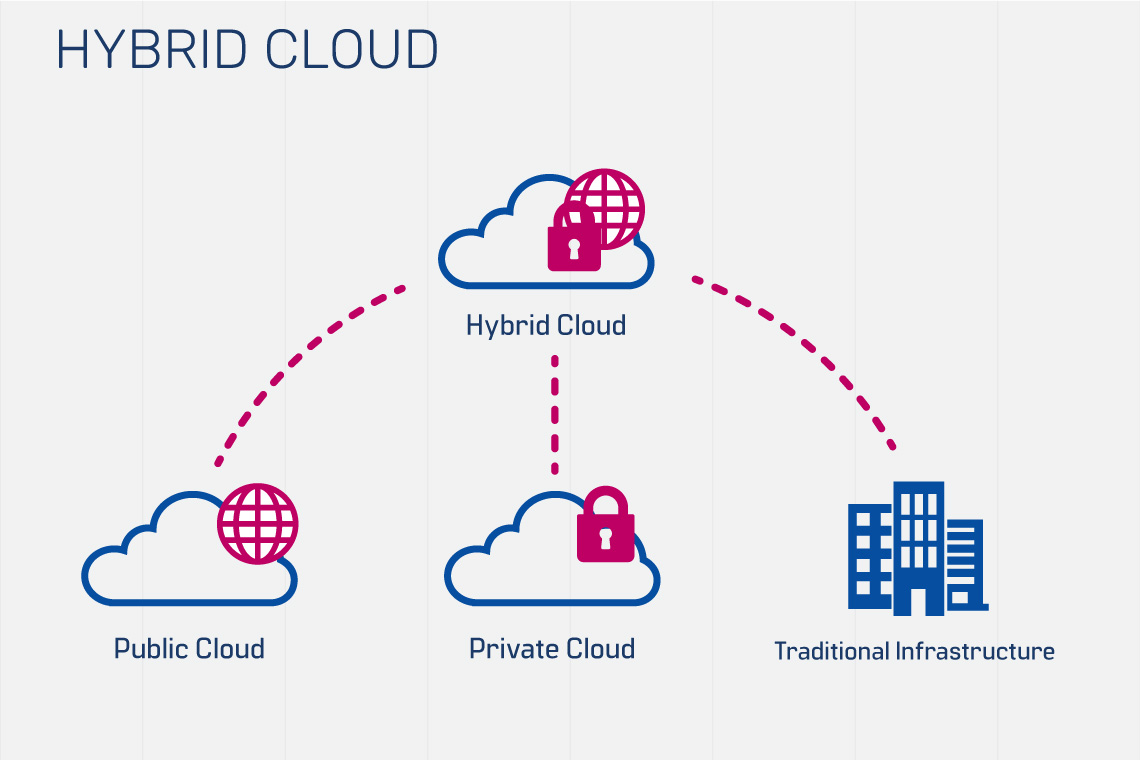
Hybrid Cloud Networking:
Hybrid cloud combines on-premises infrastructure with cloud resources(public+private), creating unique networking challenges and solutions.
The basic purpose of a hybrid cloud is to make the most of all environments, choosing to keep some data completely restricted to the four walls of an office/network while enabling others to be accessed remotely.
In the Hybrid cloud, non-critical activities are performed by the cloud resources and critical activities are performed by the on-premises resources.
Key Points:
Hybrid Cloud Architecture: Hybrid cloud networking involves integrating on-premises networks with private and public cloud networks to enable seamless communication.
Flexible and secure: It provides flexible resources because of the public cloud and secure resources because of the private cloud.
Connectivity Solutions: Cloud providers offer solutions like Virtual Private Network (VPN) connections for secure communication between on-premises and cloud environments.
Data Integration: Hybrid cloud networking allows data to flow between on-premises data centers and cloud resources.
Use Cases:
Gradual Migration: Organizations can migrate certain workloads or sensitive data to the cloud while keeping critical applications on-premises.
Resource Bursting: During peak demand, organizations can scale up by leveraging cloud resources without overloading on-premises infrastructure.

